Springboot實現(xiàn)XSS漏洞過濾的示例代碼
前陣子做了幾個項目,終于開發(fā)完畢,進入了測試階段,信心滿滿將項目部署到測試環(huán)境,然后做了安全測評之后.....
 (什么!你竟然說我代碼不安全???)
(什么!你竟然說我代碼不安全???)
然后測出了 Xss漏洞 安全的問題
解決方案場景:可以在頁面輸入框輸入JS腳本, 攻擊者可以利用此漏洞執(zhí)行惡意的代碼 !
問題演示
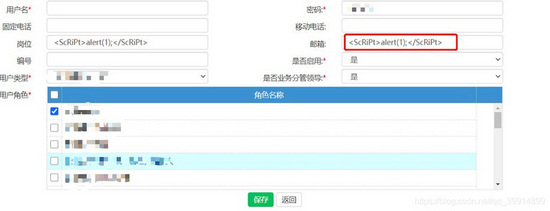
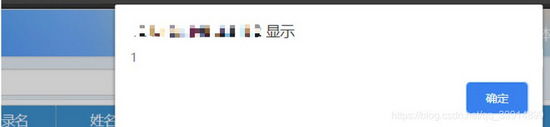
所以我們要對于前端傳輸?shù)膮?shù)做處理,做統(tǒng)一全局過濾處理
既然要過濾處理,我們首先需要實現(xiàn)一個自定義過濾器
總共包含以下四部分
XssUtil XssFilterAutoConfig XssHttpServletRequestWrapper XssStringfJsonDeserializer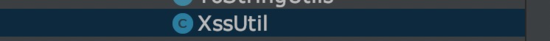

最后我們需要在全局過濾器中使用我們實現(xiàn)的Xss自定義過濾器
代碼實現(xiàn)XssFilterAtuoConfig實現(xiàn)代碼
import com.fasterxml.jackson.databind.ObjectMapper;import com.fasterxml.jackson.databind.module.SimpleModule;import net.greatsoft.overallbudget.filter.SimpleCORSFilter;import org.springframework.boot.context.embedded.FilterRegistrationBean;import org.springframework.context.annotation.Bean;import org.springframework.context.annotation.Configuration;import org.springframework.context.annotation.Primary;import org.springframework.http.converter.json.Jackson2ObjectMapperBuilder;import org.springframework.http.converter.json.MappingJackson2HttpMessageConverter;/** * Created by wjy on 2020/11/5. * xss 自動配置類 */@Configurationpublic class XssFilterAtuoConfig { /** * 注冊自定義過濾器 * @return */ @Bean public FilterRegistrationBean xssFiltrRegister() { FilterRegistrationBean registration = new FilterRegistrationBean(); //設(shè)置系統(tǒng)過濾器 (setFilter就是你所定義的過濾器filter類) registration.setFilter(new SimpleCORSFilter()); //過濾所有路徑 registration.addUrlPatterns('/*'); //過濾器名稱 registration.setName('XssFilter'); //優(yōu)先級 registration.setOrder(1); return registration; } /** * 過濾JSON數(shù)據(jù) * @return */ @Bean @Primary public MappingJackson2HttpMessageConverter mappingJackson2HttpMessageConverter() { SimpleModule module = new SimpleModule(); //自定義序列化過濾配置(XssStringJsonDeserializer), 對入?yún)⑦M行轉(zhuǎn)譯 module.addDeserializer(String.class, new XssStringJsonDeserializer()); // 注冊解析器 ObjectMapper objectMapper = Jackson2ObjectMapperBuilder.json().build(); objectMapper.registerModule(module); return new MappingJackson2HttpMessageConverter(objectMapper); }}
XssHttpServletRequestWrapper實現(xiàn)代碼
/** * Created by wjy on 2020/11/5. * xss 包裝 */public class XssHttpServletRequestWrapper extends HttpServletRequestWrapper { public XssHttpServletRequestWrapper(HttpServletRequest request) { super(request); } /** * 對header處理 * @param name * @return */ @Override public String getHeader(String name) { String value = super.getHeader(name); return XssUtil.cleanXSS(value); } /** * 對參數(shù)處理 * @param name * @return */ @Override public String getParameter(String name) { String value = super.getParameter(name); return XssUtil.cleanXSS(value); } /** * 對數(shù)值進行處理 * @param name * @return */ @Override public String[] getParameterValues(String name) { String[] values = super.getParameterValues(name); if (values != null) { int length = values.length; String[] escapseValues = new String[length]; for (int i = 0; i < length; i++) {escapseValues[i] = XssUtil.cleanXSS(values[i]); } return escapseValues; } return super.getParameterValues(name); } /** * 主要是針對HandlerMapping.URI_TEMPLATE_VARIABLES_ATTRIBUTE 獲取pathvalue的時候把原來的pathvalue經(jīng)過xss過濾掉 */ @Override public Object getAttribute(String name) { // 獲取pathvalue的值 if (HandlerMapping.URI_TEMPLATE_VARIABLES_ATTRIBUTE.equals(name)) { Map uriTemplateVars = (Map) super.getAttribute(HandlerMapping.URI_TEMPLATE_VARIABLES_ATTRIBUTE); if (Objects.isNull(uriTemplateVars)) {return uriTemplateVars; } Map newMap = new LinkedHashMap<>(); uriTemplateVars.forEach((key, value) -> {if (value instanceof String) { newMap.put(key, XssUtil.cleanXSS((String) value));} else { newMap.put(key, value);} }); return newMap; } else { return super.getAttribute(name); } }}
XssStringJsonDeserializer代碼實現(xiàn)
/** * Created by wjy on 2020/11/5. * 基于xss的JsonDeserializer */public class XssStringJsonDeserializer extends JsonDeserializer<String> { @Override public Class<String> handledType() { return String.class; } @Override public String deserialize(JsonParser jsonParser, DeserializationContext deserializationContext) throws IOException { return XssUtil.cleanXSS(jsonParser.getValueAsString()); }}
XssUtil代碼實現(xiàn)
/** * Created by wjy on 2020/11/5. * xss工具類 */public class XssUtil { public static String cleanXSS(String value) { if (Objects.isNull(value)) { return value; } //在這里自定義需要過濾的字符 value = value.replaceAll('<', '& lt;').replaceAll('>', '& gt;'); value = value.replaceAll('(', '& #40;').replaceAll(')', '& #41;'); value = value.replaceAll('’', '& #39;'); value = value.replaceAll('eval((.*))', ''); value = value.replaceAll('['’][s]*javascript:(.*)['’]', ''''); value = value.replaceAll('<script>', ''); return value; }}
全局過濾器實現(xiàn)
@Componentpublic class SimpleCORSFilter implements Filter { @Override public void doFilter(ServletRequest req, ServletResponse res, FilterChain chain) throws IOException, ServletException { // 在這里,使用我們實現(xiàn)的XSS過濾器 XssHttpServletRequestWrapper request =new XssHttpServletRequestWrapper((HttpServletRequest) req); HttpServletResponse response = (HttpServletResponse) res; response.setHeader('Access-Control-Allow-Origin', '*'); response.setHeader('Access-Control-Allow-Methods','POST, GET, PUT, OPTIONS, DELETE'); response.setHeader('Access-Control-Max-Age', '3600'); response.setHeader('Access-Control-Allow-Headers','Origin, X-Requested-With, Content-Type, Accept, token');chain.doFilter(request, response); } public void init(FilterConfig filterConfig) { } public void destroy() { }}
到此這篇關(guān)于Springboot實現(xiàn)XSS漏洞過濾的示例代碼的文章就介紹到這了,更多相關(guān)Springboot XSS漏洞過濾內(nèi)容請搜索好吧啦網(wǎng)以前的文章或繼續(xù)瀏覽下面的相關(guān)文章希望大家以后多多支持好吧啦網(wǎng)!
相關(guān)文章:
1. js select支持手動輸入功能實現(xiàn)代碼2. PHP橋接模式Bridge Pattern的優(yōu)點與實現(xiàn)過程3. asp.net core項目授權(quán)流程詳解4. html中的form不提交(排除)某些input 原創(chuàng)5. CSS3中Transition屬性詳解以及示例分享6. bootstrap select2 動態(tài)從后臺Ajax動態(tài)獲取數(shù)據(jù)的代碼7. vue使用moment如何將時間戳轉(zhuǎn)為標(biāo)準(zhǔn)日期時間格式8. 開發(fā)效率翻倍的Web API使用技巧9. jsp文件下載功能實現(xiàn)代碼10. ASP常用日期格式化函數(shù) FormatDate()
 網(wǎng)公網(wǎng)安備
網(wǎng)公網(wǎng)安備